Chaffing and winnowing
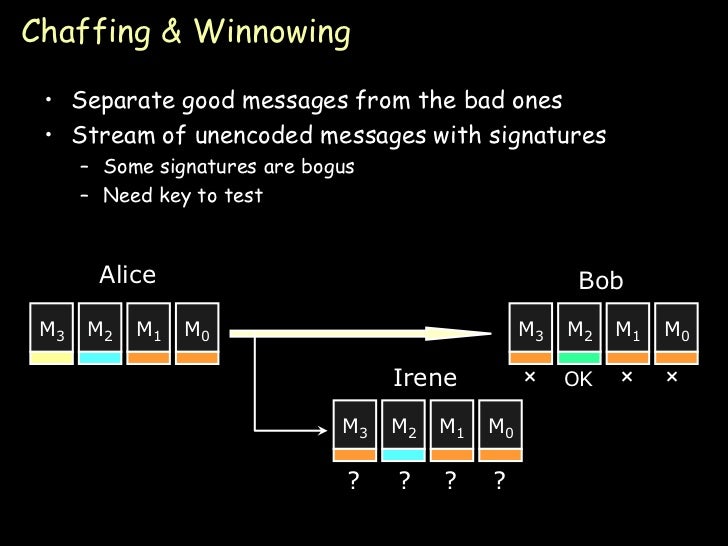
Chaff and wheat algorithm or chaffing and winnowing ( English for " move with chaff and winnowing " ) denotes an algorithm for confidentiality when sending data without the data must be encrypted. The method was introduced in 1998 by Ronald L. Rivest, and provides an alternative to steganography and cryptography represents the basic idea is the split secret message like needles in a haystack of irrelevant, but similar-looking data to hide.
Principle method on the sender side
There is the following scenario: Someone wants to sensitive data over an insecure communication channel, such as the Internet, send it to a recipient. It must be ensured by the method used, that a third party has no mitlauschender opportunity to gain knowledge of the contents of the message.
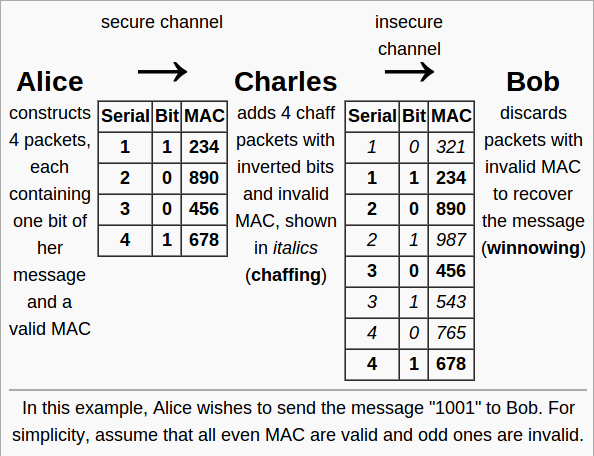
Step 1: Divide the message into packets
The sender divides the message to be sent in individual packets. The data packets are provided with a consecutive serial number. By the serial number missing or duplicate packets can be identified and finally reconstructs the message to the recipient.
Step 2: Authentication
The sender authenticates each packet with a secret key that is known only to the sender and receiver. The sender for each data packet adds a Message Authentication Code (MAC ) is added. This code is calculated from the serial number, the actual data and the key. As an algorithm for the calculation of the HMAC -SHA1 algorithm is used for example.
Step 3: Add a chaff
It be mixed further, not to the actual message data packets belonging. In these packages, the requirements are made to contain matching serial numbers and seemingly meaningful data. It will be added to any MAC.
Finally, it is important that the MAC for this package is incorrect. But do not you need the actual authentication key. Step 3 can therefore be performed by an uninvolved third party.
Principle method on receiver side
The receiver verifies the authenticity of each incoming packet. For this he calculated from the serial number, the data and the means available for its part, the MAC key and compares it with the received. The authentic packets are buffered and assembled in the port based on the serial numbers.
Features of the method
To ensure with chaffing and winnowing a certain security against eavesdropping, the volume of transmitted data needs to be significantly increased by irrelevant content " chaff ". Furthermore, the actual data must ( the message ) are fragmented enough so that individual fragments have little or no relevance for themselves.
The authentication key is a secret key, which may be only the sender and the receiver of the message. The transmitter and the receiver may at any time arrange a new secret authentication key, such as the Diffie- Hellman method.
Application in the blogosphere
Due to the myriad of weblogs that are orphaned in many cases, and a large volume of comment in the blogosphere, the use of chaff and wheat algorithm there is also conceivable. The existing, genuine comments correspond to the chaff.
Sender and receiver agree on a selection of blogs. The selected blogs can be independent. This definition represents a symmetric key
The message to be embedded is divided into parts and posted in the agreed upon blogs as a comment. To prevent posts of this nature will be deleted as spam, it makes sense, to enrich for more chaff shares within the comment that make the comment appear plausible as expression. Moreover, the application of linguistic steganography to disguise the individual message parts is useful.
The method requires a relatively high level of redundancy, since off-topic comments will be deleted quickly in well maintained blog. Underused or orphaned blogs therefore offer more suitable for blog Steganogramme, since there can be expected with little comment moderation. On the problem of the persistence of blog comments can be: Abgeschickte comments you can not remove yourself from the blogs in general. Attacker could gain the key, so the blogs, in which is posted, and their order, he can reconstruct the original message.
Mistakenly, this approach is sometimes referred to as a blog steganography, although it does not need in principle without steganographic methods.
General example for the algorithm
It should be the following message sent secret:
" Hello Bob, see you tomorrow at 12h. Alice "
After step 1 and 2, the following packages are available: ( all data packets have the form serial number, message, MAC)
- (2, see you tomorrow at, 782 290 )
- (3, 12h. , 344287 )
- (4, Alice 312265 )
With Step 3 chaff is added:
- (1, Hello Larry, 532 105 )
- (2, we talk tomorrow at, 793 122 )
- (3, 16h. , 891 231 )
- (4, Susan, 553 419 )
On the communication channel, the following messages are transmitted:
- (1, Hello Larry, 532 105 )
- (1, Hi Bob, 465231 )
- (2, see you tomorrow at, 782 290 )
- (2, we talk tomorrow at, 793 122 )
- (3, 12h. , 344287 )
- (3, 16h. , 891 231 )
- (4, Susan, 553 419 )
- (4, Alice 312265 )