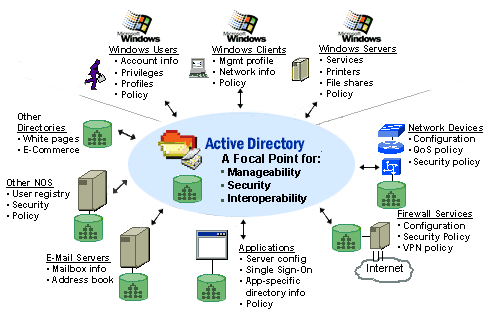
Active Directory
Active Directory (AD ) is called the directory service of Microsoft Windows Server, which is divided from the version of Windows Server 2008, the service in five reels and whose core component is referred to as Active Directory Domain Services ( ADDS ).
In such a directory (English: directory ) is a list of assignments such as a phone book, the phone numbers to the respective terminals ( owners ) assigns.
Active Directory makes it possible to divide a network according to the real structure of the company or its spatial distribution. To this end, it manages various objects in a network, such as users, groups, computers, services, servers, file shares, and other devices such as printers and scanners and their properties. With the help of Active Directory, an administrator can organize, deploy, and monitor information of the objects.
The users of the network can access restrictions are granted. So, for example, may not every user view each file or use any printer.
- 3.1 components
- 3.2 database
- 3.3 Objects 3.3.1 Object categories
- 3.3.2 Storage in containers ( OUs )
- 3.4.1 Wald ( forest )
- 3.4.2 Organizational Units
- 3.4.3 location
- 4.1 Windows NT
- 4.2 In Windows 2000: Multi- Master Replication
- 6.1 Samba
- 6.2 eDirectory
- 6.3 FreeIPA
Server Roles
Since Windows Server 2008, the term Active Directory five different server roles summarized:
- Active Directory Domain Services ( Active Directory directory service domain, ADDS ) is the current version of the original directory service and the central point of the domain, and resource management.
- Active Directory Lightweight Directory Services ( Active Directory Lightweight Directory Service, ADLDS ) is a functionally limited version of ADDS, which is used to connect applications or services that require LDAP -compliant information from the directory. For the first time in Windows Server implemented in 2003, the service was there known as Active Directory Application Mode (ADAM ).
- Active Directory Federation Services ( Active Directory Federation Services, ADFS ) are used for web-based authentication of users when they are in areas outside the ADDS infrastructure.
- Active Directory Rights Management Services ( Active Directory Rights Management Services, ADRMS ) protect resources by cryptographic methods to prevent unauthorized access.
- Active Directory Certificate Services ( Active Directory Certificate Services ADCS ) provide a public-key infrastructure.
The four main components
Lightweight Directory Access Protocol (LDAP)
The LDAP directory provides, for example, information about users and their group membership. However, other objects, such as a computer, the certificates are stored in the directory. LDAP itself is not a directory but a protocol by which it is possible using a specific syntax to query information in an LDAP directory.
Kerberos protocol
Kerberos is a protocol with which the user is authenticated, so that he (TGT ) is replaced by a so-called " Ticket Granting Ticket ". With this it is possible to obtain service tickets for access to a specific service within the network. The user has to enter his password only once to obtain the TGT. The procurement of the service ticket is then carried out in the background.
Common Internet File System ( CIFS)
The CIFS protocol is intended for the storage of files on the network. This DNS to locate the individual computer systems and information service (SRV Resource Record) will be used. It also provides a way to connect to the Internet due to the standardized protocol dar.
Domain Name System (DNS)
Unlike earlier versions of Windows, such as Windows NT 4.0, which used for NetBIOS name resolution, a private DNS is required for Active Directory. To be fully functional, the DNS server must support SRV resource records.
For reasons of compatibility Windows 2000 - or XP clients with appropriate configuration even when using an Active Directories still be able to find out, using NetBIOS or WINS network resources.
Construction
Components
Active Directory is divided into three parts: schema, configuration, and domain.
- A schema is a template for all Active Directory entries. It defines both object types, classes and their attributes and their attribute syntax. What types of objects in Active Directory are available, can be influenced by the definition of new types. For the underlying pattern is the " pattern " which define the objects and their attributes.
- The configuration also represents the structure of the Active Directory forest and its trees
- The domain finally contains all information describing themselves and the objects created in it.
The first two parts of Active Directory are replicated between all domain controllers in the forest, while the domain - specific information are available only within the domain in question, ie on their respective domain controllers. Therefore exists in every domain in addition a so-called Global Catalog. He represents all information on your own domain and also contains important part of information of the domain of the forest and thus allows, for example, domain -wide search operations.
Database
The Active Directory used to store the information about the network objects a Jet ( Blue ) database that uses Microsoft for the Exchange server. It is relational, transactional and uses a " Write-Ahead Logging". The Active Directory database is limited to 16 terabytes, and each domain controller can create up to 2 billion objects.
The database file " NTDS.DIT " contains three main tables: the "schema table" to store the schemas, the "link table" to store the object structure and the "data table" to store the data.
ESE ( Extensible Storage Engine ) assigns the stored according to a relational model, Active Directory data according to a predetermined scheme in a hierarchical model.
In Windows 2000 Active Directory uses the Jet -based ESE98 database.
Objects
In contrast to object-oriented system directory Novell's eDirectory, Active Directory is more than object-based - should be called - and hierarchically.
The records in the database are defined in the Active Directory as "objects " and their properties as " attributes ". The attributes are defined depending on their type. Objects are uniquely identified by their name.
The Group Policy settings are stored in Group Policy objects. These are also associated domains and locations.
Object categories
Objects can be divided into two main categories:
- Accounts, such as user, group and computer accounts
- Resources, such as file and printer sharing
Storage in containers ( OUs )
The possibly up to many millions of objects are called in containers ( OUs ), and OU ( Organizational Unit), filed. Some containers are pre-defined, any other organization units can be created with sub-units ( OUs under it ). As an object- based system, Active Directory supports the inheritance of properties of an object container to child objects that can be container again. This allows Active Directory to build networks logically and hierarchically.
Hierarchy
Wald ( forest )
The entire hierarchical structure is called "Forest " ( forest ) or " forest "; a collection of all objects, their attributes, rules and containers are stored in the directory. The Forest manages one or more transitive linked trees. A tree maintains one or more domains, which in turn are transitive in the hierarchy are linked. Domains are named according to the rules of the DNS system, the " namespace" ( namespace).
Organizational units
An organizational unit (OU ) is a container object that is used to group other objects in AD. An OU can contain objects alongside other OUs. The user-defined hierarchy of OUs simplifies the administration of Active Directory. They usually depends on the network structure ( network management model) or by the organizational structure of the company. The OUs are the lowest level of Active Directory, can be divided into the administrative rights.
Location
One way the subdivision is a location. This represents a physical grouping of one or more logical IP subnets
Sites are characterized by the connection between slow networks such as WAN or VPN on the one hand and fast networks, such as LAN on the other. Domains can contain locations and sites may include domains. This is important for the control of network traffic caused by replication operations.
It is fundamental to plan the infrastructure of the enterprise information carefully in a hierarchical division into domains and OUs. For this, allocations have been useful in terms of geographic locations, tasks or IT roles or a combination of these models.
Domain Controller and Replication
Windows NT
In Windows NT, there was always an excellent controller per domain, the primary domain controller (PDC), was allowed to perform the changes to the user and computer database (SAM ). All other domain controllers serving as a backup that can be upgraded if necessary to a PDC.
Starting with Windows 2000: multi-master replication
Active Directory uses for replication of the directory between domain controllers, a so-called multi-master replication. This has the advantage that describe and synchronize each replica can. Thus, in distributed implementations, a local administration is completely possible. Unlike NT4 domains have Windows 2000 or any domain controller (DC ) is a writable copy of the Active Directory database. The change of an attribute on one of the DCs is transmitted at regular intervals to all other DCs ( replicated ). This means that all DCs on the same stand Failure of DCs is irrelevant to the Active Directory database, since no information is lost. The replication interval can be adjusted depending on the frequency of changes to 15 or more minutes. Windows 2000 Server replicates the AD default after no more than five minutes, Windows Server 2003 replicates it by default for more than 15 seconds. As replication proceeds at most 3 hops, you get depending on the server version used 15 minutes and 45 seconds as the replication interval for a domain.
Naming
Active Directory supports a naming and access via UNC/URL- and LDAP URL names. Internally, the LDAP version X.500 is used for the name structure. Each object has a fully qualified name ( distinguished name DN). A print object is, for example, " LaserDrucker3 " in the organizational unit "Marketing" and the domain " foo.org ". The fully qualified name is therefore " CN = LaserDrucker3, OU = Marketing, DC = foo, DC = org". "CN" stands for " common name". "DC" is the domain object class ( domain component ), which may consist of many parts. The objects can also be referred to by the UNC / URL notation. This is characterized by a reverse sequence of identifiers, which are separated by slashes. The above object could thus also be called " foo.org/Marketing/LaserDrucker3 ". To address objects within the container, relative names are used (relative distinguished names, RDNs ). This would be for the laser printer, "CN = LaserDrucker3 ". Each object has beside his globally unique name for an equally globally unique 128-bit number ( globally unique identifier GUID). This is usually represented as a string and does not change even when you rename the object. Furthermore, each user and computer object can also clear about its associated UPN ( User Principal Name ) to be addressed, which has the structure " Object " @ " domain name ".
Alternatives to Windows Server
Samba
In addition to Windows Server and the free software Samba can provide an Active Directory directory service available for Linux and UNIX systems. The current version 4 includes a complete implementation of Active Directory and can thus replace a Windows server completely in this regard. This was not least because of the support that had received the Samba project from Microsoft directly, possible.
EDirectory
Similar functions such as Active Directory provides developed by Novell eDirectory. It is available for Windows and for Linux and Active Directory also allows different than managing a heterogeneous IT infrastructure. By means of the essay Domain Services for Windows eDirectory can emulate an Active Directory.
FreeIPA
The relatively young FreeIPA project of the company Red Hat brings together existing open-source technologies to create a free alternative to proprietary products Active Directory and eDirectory. Because FreeIPA currently still in development, all the capabilities of Active Directory are not yet available and it is only available for Unix and Linux systems.




.jpg)