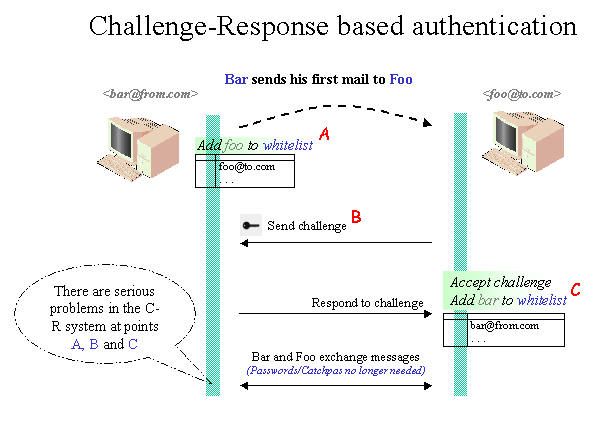
Challenge–response authentication
The challenge-response method (translated as prompt - response method ) is a secure authentication scheme based on a participant's knowledge. Here is a participant in a task (german challenge) that the other must (English response) to prove resolve that he knows certain information ( shared secret ) without transmitting this information itself. This is a safeguard against the fact that the password by attackers can be heard on the line.
For this purpose there is in detail different methods that are based on this basic principle: If a page (usually named in cryptography as Alice) and another side wants to authenticate (usually called Bob ), then Bob sends a random number N ( nonce ) to Alice ( so Bob, the Challenge ). Alice adds this number N by their password, applies a cryptographic hash function or encryption on this combination and sends the result to Bob ( and thus provides the response). Bob, who knows the random number as well as the shared secret ( password = Alice ) and the hash function or encryption used, performs the same calculation and compares its result with the response that he receives from Alice. Are two dates are identical, then Alice has successfully authenticated.
Attacks
An attacker who is listening on the line, but has the ability to launch a so-called known-plaintext attack. To this end, it records the transmitted random number ( challenge) and the corresponding response and tries to infer the password used with cryptanalytic methods. Such attacks have led, for example, in GSM systems to success. A further possibility in the dictionary attack. Here the attacker guesses the password to encrypt the random number and compares its result with the response. In this way, the version 4 of the Kerberos protocol could be successfully attacked. Remedy in this case, for example, the encrypted transmission of the random number from Bob to Alice. Another way to substantially prevent this chosen-plaintext attack, the additional inclusion of a valid only for a short time timestamp in the Challenge, so that the validity of the response expires before the attacker can guess the password. To retransmitting ( replay attack ) to make a caught Response unsuccessful, must also be ensured that the random number in the Challenge will change with each connection or session and a long-term collection of Response responses by the attacker is not worthwhile; This is achieved by the end of the time stamp.
Depending on the hash method can now be calculated by brute force in one to two days the secret. That is why such authentication should be performed only within secure compounds.
Disadvantages
All passwords are required on the server side in plain text, to this must be in plain text or decrypted plaintext again. There is thus the possibility that there passwords can be tapped by a third party. In a publication of user data, the password can be communicated in plain text without any extra effort.
Another disadvantage is that even on the client side ( Alice) must be the secret in plain text, the client may be unjustified to spend so that as a user. However, this can be addressed by a response which is calculated on a smart card, then you have the problem again that you must ensure that no unauthorized person uses Alice's smart card.
Application
Applications is the challenge-response authentication in the APOP authentication method the POP3 protocol or CHAP authentication for PPP network connections (eg ADSL or dial-up Internet connections).
Apple 's version of the VNC protocol for screen sharing also uses a challenge-response system of registration.