Revocation list
A CRL ( certificate revocation list english CRL) is a list that describes the invalidation of certificates. It makes it possible to determine whether a certificate has been revoked or canceled, and why.
Certificates are revoked or revoked if their associated keys are no longer safe, for example, because they are falling into the wrong hands or were "cracked" - in such cases, the certificate must be locked before the actual expiration date, so the key is not is used. Another reason for the restriction or revocation of a certificate might be a false certificate content, for example in the case of a name change. CRLs are therefore an important part of the Public Key Infrastructure.
A lock ( engl. hold) is temporary and can be reversed (eg if you are not sure if the private key is lost / compromised, but you want to be sure ), a revocation (English revocation ) is final.
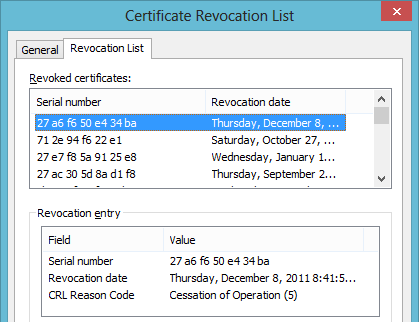
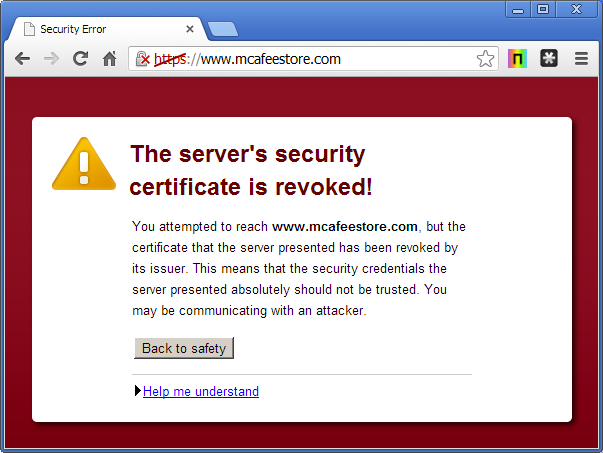
Explains a certification authority (English certificate authority, CA), a certificate (or several) to be invalid, it shall bear the serial number of the certificate in the Certificate Revocation List. This is always requested when a program requests to the certification authority, whether a given certificate is valid ( what should be done before each use of the key ).
The revocation list containing a timestamp and is safe from manipulation itself secured by a digital signature. Thus, a software that evaluates this block list, verify that the integrity of the lock list is guaranteed and whether it comes from a trusted publisher.
At the blacklist also includes a validity period, outside of which the information in the list I just want to no longer considered valid. An application is after the validity period has expired, download the current version of this list by the issuing CA.
Such revocation lists are theoretically quite easy to create and manage, but are so far rarely used in practice. The problem is that a program before using a key always on the certificate authority must consult - which presupposes that an internet connection exists. If there is no connection, the certificate can not be verified, then it is possible that a key is used, which is already known to unauthorized persons.
X.509 v2 CRL structure of a
- Version
- Producer of the CRL
- Algorithm for the signature
- Update time of issue of this CRL
- Update time of the issuance of the next CRL
- List of withdrawn certificates (serial number and date of withdrawal)
- Extensions
Problems
Revocation lists are by definition negative lists and can thus give a user no information as to whether a certificate is valid. Nor can it provide information on whether a certificate was ever issued by a certification authority.
In addition, CRLs make statements about the past; it can not be examined in the light of such a list, if at a certain moment a certificate is recalled.
A newer protocol for querying the certificate validity is the Online Certificate Status Protocol (OCSP ), which was developed to resolve problems of CRLs. OCSP implementations, however, often put on blacklists, so that is where the problems were merely shifted.