User profile
A user profile is a configuration in system administration an account with an operating system, a computer network or in a processing site. These data are centrally managed in a special directory ( collection point ). The user profile of computers containing the user rights of one or more users and their personal settings.
Computer
The user profile may include various rights, such as read access, write access, connections, installation of programs and delete rights. These rights are assigned by the system administrator in the user management and can be changed by any other system administrator. The administrator, however, has "only" a - privileged - user profile. To ensure privacy, user profiles are other principle limited by it.
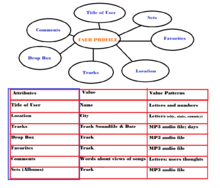
In the user profile also personal data and the individual user settings are saved:
- Desktop Content
- Designing the user interface
- E -mail accounts and associated data directories
- Links
- Internet bookmarks
- Digital certificates
- Cookies
- Passwords
- Configuration files of programs of any kind, such as installing software, changes to programs, Internet connection
Particularly sensitive data are often additionally secured, such as the root account on Unix or " protected memory " on Windows. For large networks, the flexibility can be obtained by a server stored on the Roaming User Profiles ( freely translated as " freely moving user profile " ) can be increased. The user can then use it to access from any computer on the network to the personal profile. However, this requires a very homogeneous software and hardware environments with the same software versions. If this is not the case, can be used and managed, for example, with Citrix Presentation Server is a platform-independent user profile is not loaded on a local computer and is processed there, but always remains on the server.
User IDs
As a rule, user profiles are protected by a user ID and a password. To ensure the security significantly increase (especially in at-risk or high - privileged sections ), the user ID should be treated as non- public information. In particular, e- mail addresses and schemes should be avoided as firstname.lastname. It is recommended to use instead not derivable strings or to make a combination of external features with a non- guessable component. In addition, make sure that the application is no evidence of the presence of user IDs.
Passwords
The use of secure passwords can be achieved in that the user's system does not accept any desired by the user password and pretends rules and compliance checks. Generally recommended that passwords of simple dictionary words, personal information (name, birthday, etc. ) and simple number combinations are avoided. It is recommended that a combination of ( intentionally misspelled ) words, special characters, upper and lowercase letters and numbers. For larger networks a mandatory periodic password change can be useful.
Mobile phone
Most mobile phones offer so-called profiles ( environments ). The operator can select settings and enable or disable as necessary depending on the environment conditions (air, meeting, vehicle, etc.). A fictional setting "home" for example, would call signaling: a ( sub-item tone and vibrate mode: active), Ringing volume: 5, Increasing volume: from. After power is usually the last used user profile active. The Mute ( "Mute ") is a user profile.