Bridging (networking)
A Bridge ( German " Bridge") connects the two computer network segments at the level of layer 2 (data link layer ) of the OSI model. A bridge can operate at the MAC sub-layer, or sublayer LLC. It is then called a MAC bridge or LLC - Bridge. A further distinction arises from the nature of the routing path of data packets in transparent bridge and Source Routing Bridge.
A MAC Bridge ( IEEE 802.1D ) is mainly used to divide a network into different collision domains. Thus, the load in large networks can be reduced, since each network strand receives only the packets whose receiver is also located in this network. Also served such Bridges are to couple sites over usually slower WAN links, such as ISDN or X.25 each other.
A MAC bridge connects networks with the same access method. The LLC bridge (also called remote bridge or translation bridge) is used two subnetworks with different access methods to couple (e.g., CSMA / CD and Token - passing) and is ( idealized ) consists of two parts which are connected to each other, the medium between the two parts this does not matter. Within the LLC - Bridge implementation (translation ) takes place. In this reaction, all parameters of the source network (such as MAC address, size and structure of the MAC frames ) are adjusted to the destination network, where they are supported by the target network. Such translation is not always directly possible. Incompatibility of the networks partially the detour via router functionality has to be gone.
A transparent bridge learns which MAC addresses in what subnet are. The bridge learns potential recipient by the sender of packets in each subnet be entered in an internal forwarding table. Using this information, the bridge determine the path to the receiver. The sender addresses are continuously updated in order to detect changes immediately. A source routing bridge has no forwarding table. Here, the transmitter must provide the information to be forwarded to the destination.
A package must be only sent to all subnets if the recipient is not registered in this table and the destination network is therefore not known. A broadcast is always transmitted in each subnet.
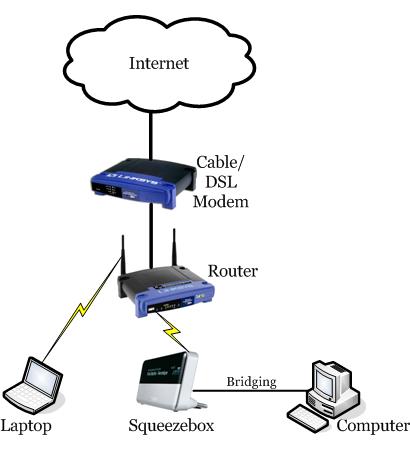
An easily understood example of a Bridge is a laser bridge that enables data exchange between two buildings by laser beam. In each building is a part which consists of a network port, and a laser transmitter and receiver unit while the two network ports are in the same logical network.
Allen Bridge types have in common is that their (network ) ports operate in promiscuous mode, all packets are received, then a check (checksum ), so that only the correct frames retransmitted. Further, each incoming packet is sent to all ports in the unlearned state ( except the port to which the packet was sent ).
Bridges can be configured redundantly to compensate for the failure of a bridge. In order to suppress the multiple forwarding of data packets, has a suitable communication protocol, such as the Spanning Tree Protocol or trunking, meshing, etc. are supported.
Bridges vs. switches
There is in the literature no clear division of technology, define the bridges or switches. Switches operate as transparent bridges, but have a higher throughput and more ports. Add to that modern switches are also often equipped with a Layer 3 Instance, a simple router. General Bridges have been around since 1985 for segmenting ( reducing the collision domain ) of networks and for connecting different architectures ( eg Ethernet - Token Ring ) developed and marketed. Switches were not developed until much later (1990). You can replace the router, under certain circumstances, even if they do not contain their own Layer 3 Instance. For example, if the use of a switch instead of a bridge was needed to shrink a collision domain and a bridge did not have enough ports and throughput.
To reduce the size of the collision domain switch receives as many ports to which only a few devices - ideally one - is connected. In addition, provide one or more so-called uplink ports connections forth to the next switch or router. Often, but not necessarily uplink ports are realized in a more rapid or higher ( Ethernet ) technology as the other ports (e.g., gigabit Ethernet instead of Fast Ethernet or fiber-optic cable instead of copper twisted pair cables). Not modular switches have a minimum of four to a maximum of about 48 ports in general. Great " modular " switches can be configured into units with several hundred ports depending on the model. In contrast to bridges, switches can transmit multiple packets simultaneously between different port pairs. Most willing to a bridge corresponds to a switch in the mode Store and forward, usually with only two ports: a switch is a multiport bridge ( a switch is a multiport bridge) was in 1991 a teaching award from Cisco Systems, since the takeover by Kalpana in 1994 is one differentiated deal with the issue at Cisco.
In the early days of the switch technique also port switches were common, which were less expensive devices, which possessed a dedicated uplink port and were able to save to the remaining ports only one MAC address per port. Bridges, however, can always save a lot of MAC addresses in their internal SAT ( Source Address Table). Conversely need bridges for connecting multiple devices often external distribution such as hubs.
In general, bridges and switches networks with different transmission speeds can connect with each other. Bridges can usually work on both MAC and LLC on base, on the other hand switches work for MAC. Switches can therefore no different architectures (eg Ethernet - Token Ring ) bridge. Since Ethernet is dominating the market, bridging different LAN architectures has only minor importance. Not least because bridges are now niche products.
For larger switches, just as with powerful Bridges, a certain bandwidth can be set for each connected network segment, also certain to prioritize services (Flow Control). In addition, large modern switches support a variety of protocols and procedures (eg, discovery protocols, VLANs, MANs, QoS, Layer 3 Instance with various routing protocols, management protocols (SNMP, RMON, Syslog ), infrastructure protocols ( DHCP server, BOOTP / TFTP server, FTP server, SSH server), special handling of certain protocols (DHCP and BOOTP relay agent ), safety features (Layer 2-4 ACLs, Gratuitous ARP protection, DHCP enforcement, MAC Lockdown, broadcast control, ingress filter ), redundancy protocols ( VRRP ), etc.). Here also the differences routers are becoming increasingly blurred.
Bridges and virtualization
Bridges that are set within an operating system, play a major role when it comes to virtualization. Here, a so-called Bridge Device is set up, which expands a real network card to virtual network cards and connecting them as a bridge. These interfaces are provided NICs available to the virtualized guest system as a (virtual). Only through these network cards, the external network communication a guest on the network physical interface of the host system is possible and externally.
Software Bridges
In addition to dedicated hardware, you can also use your computer to Apple Mac OS, BSD, DOS, Linux or Windows XP - based as bridge solutions. Although a specific hardware works mainly robust and due to the special architecture also faster; yet just bribe Linux and BSD versions by an extensive support of various network cards and protocols. But power limiting effect the low data throughput rates and the relatively high latency of the standard on PCs bus systems. Never reach PCs, the throughput of switches and rarely by Bridges. General have software router on a PC or workstation base often another drawback: the relatively high power consumption. After just one year, electricity costs may be higher than the price of a small compact device. Some Bridges Although hardware Bridges call themselves, but are actually composed of PC components. Only the case or partly mechanically changed PCI slots and the operating system give the appearance of a special system. While these systems work usually very robust and reliable; but here also, the bridging is performed by software and without any special hardware support.
Brouter
Devices that combine the functions of bridges and routers, called occasionally brouter. More commonly found erroneously the term Layer 3 switch. However, a Layer 3 switch is not exactly the same as a brouter.